Why banks are upgrading account takeover protection in 2025
Account takeover (ATO) protection is the frontline defense that prevents criminals from using stolen or spoofed credentials to impersonate legitimate customers.
The problem is speed. In 2024, Verizon reported that phishing kits were able to harvest the first credential in under 60 seconds, while banks typically only detected fraud several hours later. That lag helped drive a staggering surge in ATO with 83% of financial institutions reporting direct business impact. In 2025, reacting after the fact is not protection, it is damage control.
Motti Tal, Chief Strategy Officer at Memcyco, puts it plainly:
“Account takeover is not new. But as exposure grows and financial opportunity for attackers increases, they invest more in researching and creating new techniques.”
The message for banks is clear: if you fail to prepare, you’re preparing to fail, and ‘preparing’ means pivoting from a reactive to preemptive posture. With the right technology, this pivot can be achieved quickly and without friction. The reasons for doing so are many.
MFA is a speedbump that can be bypassed, not protection. Takedown tools stop credential theft only after many customers are already compromised, and then can’t keep the next attack from being launched again and again. Meanwhile, attackers are adopting industrializing ATO fraud with the help of AI-powered phishing kits, and adversary-in-the-middle exploits that raise no suspicion, faster than banks can respond.
Memcyco’s Account Takeover Protection solution enables banks to move from reactive detection to real-time prevention, protecting customers before fraud losses occur.
Companion Resource
Want deeper insights?
Download our exclusive Industry Brief: Account Takeover Protection for Banks in 2025 to see the latest fraud trends, why legacy defenses are failing, and how real-time solutions can safeguard your institution.
What are the latest bank account takeover protections against evolving “ATO” fraud tactics?
Banks are under pressure to evaluate the latest ATO protection methods against an increasingly creative fraud landscape. The most effective approaches emphasize visibility and interception before attackers succeed.
1. Decoy credentials:
Stops credentials from being stolen in the first place by feeding attackers artificial, traceable credentials on fake or spoofed login pages. Prevents them from harvesting usable data during phishing or impersonation attempts.
2. Real-time compromised login interception:
Blocks logins using stolen or replayed credentials on the genuine site before attackers gain access, ensuring compromised data cannot be used for account takeover.
3. Man-in-the-middle countermeasures:
Mitigate scams using advanced ATO techniques such as reverse proxy phishing, rogue WiFi networks (Evil Twin) and DNS poisoning.
4. Device fingerprinting (Device DNA):
Associates logins with persistent device identifiers, continuously evaluated to help differentiate legitimate customers from potentially fraudulent access attempts.
5. Early takedown response:
Integrated with real-time monitoring to shorten exposure windows.
Tal highlighted the core issue:
“We identified the biggest gap: lack of visibility into what happens when a customer is invited into a phishing trap. That blind spot doesn’t have to remain.”
Learn why real-time fraud prevention outperforms takedown tools.
What is account takeover protection?
Account takeover protection is the set of controls that detect and stop cybercriminals from stealing and/or using stolen credentials to impersonate bank customers. While definitions vary, the fundamentals are clear: it prevents identity fraud at the moment of login and other critical access points.
Legacy defenses center on:
1. Multi-factor authentication (MFA):
A critical layer, and widely used, but increasingly bypassed and often a source of customer frustration.
2. Domain monitoring and takedown:
Helpful, but only reacts after phishing sites or scams are already live and have caused damage. and nothing prevents the fake site from coming live again under a different URL.
3. Suspicious login anomaly detection:
A newer safeguard, but prone to high false positives and a frequent source of customer friction.
As Tal emphasized:
“The fundamentals of ATO have always been credential theft. Once attackers have them, they can impersonate customers at will.”
Banks must move beyond these rule-based safeguards to proactive, real-time defenses. Here’s a breakdown of the steps to strengthen ATO detection.
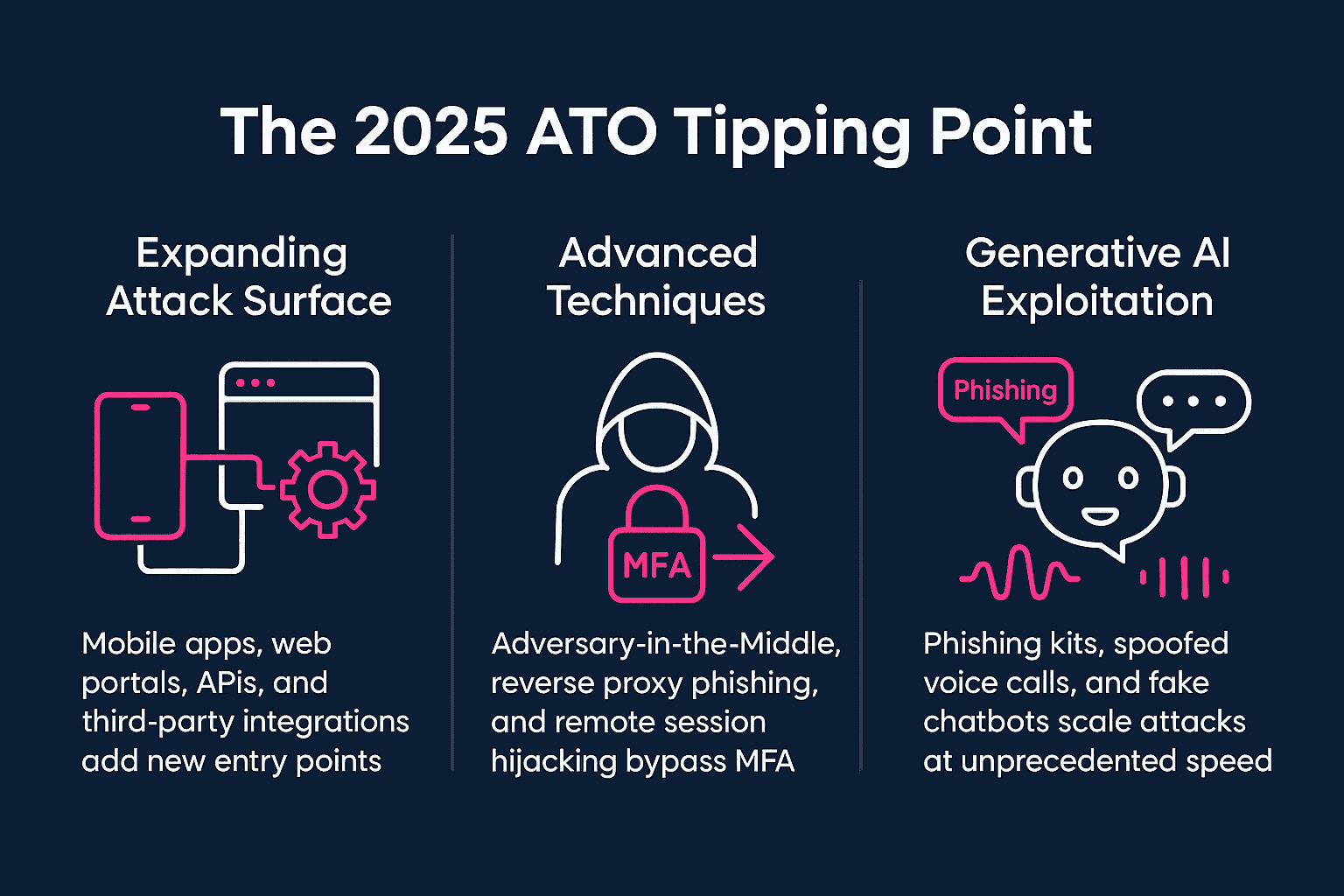
Why account takeover threats are escalating in 2025
The year 2025 marks a tipping point for account takeover fraud with the following threat amplifiers fuelling and empowering more and more scams. Banks are no longer facing isolated credential theft attempts, but a perfect storm of broader exposure, advanced attacker methods, and AI-driven automation. The result is an environment where attacks are faster, harder to detect, and more costly than ever before.
- Expanding attack surface:
- Mobile apps, web portals, APIs, and third-party integrations add new entry points.
- Advanced techniques:
- Such as Adversary-in-the-middle, reverse proxy phishing, and remote session hijacking bypass MFA.
- Generative AI exploitation:
- Phishing kits, spoofed voice calls, and fake chatbots scale attacks at unprecedented speed.
According to recent data, 50% of banking attacks are already GenAI-based, making this the fastest-growing vector in financial fraud.
Tal cautioned:
“The GenAI arms race is real. Attackers iterate faster than banks, because their investment is rewarded instantly with stolen assets.”
Read more on generative AI’s role in phishing and fraud.
Why legacy defenses are failing banks
Despite significant investments in fraud prevention, most banks still rely on legacy tools like MFA, domain monitoring, and scanning and takedown. These defenses may once have been sufficient, but today they can’t keep pace with the speed and sophistication of modern attacks. The cracks are showing, customers are paying the price, and in more and more cases, banks are required to reimburse them.
- MFA bypass and friction:
- A vital layer, widely adopted, yet increasingly bypassed and often a source of customer frustration.
- Delayed takedowns:
- Scams remain active long enough to steal credentials before removal. Even then, takedowns fail to detect all impersonating domains or provide insight into the attack.
- Customer churn:
- 45 % of customers will stop transacting with the business temporarily, and 40 % will walk away for good.
Tal put it clearly:
“Reactive approaches leave banks exposed. By the time alerts arrive, the fraud has already happened.”
Here’s why domain takedown services miss critical threats.
Key challenges banks must evaluate in ATO protection
Selecting the right ATO protection is not straightforward. Banks must weigh customer experience, visibility, and regulatory obligations all while keeping fraud losses under control. These challenges define how effective any chosen defense will be in practice.
- Balancing customer experience vs. fraud detection:
- Customers want seamless access while regulators demand stronger controls.
- Visibility gaps outside the bank’s domain:
- Most phishing and spoofing happens off-bank infrastructure.
- Regulatory drivers
- The UK already mandates reimbursement; similar rules are emerging in the US, APAC and other parts of the world.
The cost of failure is steep: 45% of customers stop transacting after an ATO incident, and 40% close accounts permanently.
See how global scam regulations are reshaping fraud liability.
Best practices for account takeover prevention in 2025
As attackers outpace traditional defenses, banks can no longer rely on outdated fraud playbooks. To stay ahead, fraud prevention leaders must adopt proactive, real-time measures that close visibility gaps, preemptively exposing scammer operations before attacks escalate.
- Move from reactive to proactive:
- Detect and block attacks before customers are compromised.
- Deploy credential decoys:
- Lure attackers into collecting false data while triggering real-time alerts.
- Use advanced device fingerprinting:
- Device DNA distinguishes attacker devices from genuine users.
- Integrate real-time monitoring:
- Track phishing sites, spoofed apps, and session hijacking continuously.
Tal summed it up:
“With real-time protection, banks move from being the last to know, to being the first to know and the first to stop fraud.”
How Memcyco delivers real-time ATO protection
While many banks still rely on reactive defenses, Memcyco provides a real-time, proactive model that exposes and helps neutralize today’s most critical ATO attacks preemptively, from their earliest inception. By embedding protective layers into every customer interaction, Memcyco delivers visibility into phishing attempts, intercepts credential theft, and enriches fraud defenses with forensic detail.
1. Nano Defenders:
Activate on the genuine site to detect phishing-driven logins in real time, identifying victims and exposing attacker devices and campaigns.
2. Decoy credentials:
Inject decoy data into phishing flows, rendering stolen credentials unusable and revealing attackers when they attempt reuse.
3. Device DNA:
Assigns persistent device identifiers and continuously evaluates them against behavioral history, flagging repeat attacker devices even when credentials change.
4. Real-time alerts and ROI:
Provides actionable alerts enriched with forensic detail, helping banks cut response time from days to hours and achieve significant operational savings.
Tal explained the impact:
“Our customers report cutting ATO handling from 72 hours to 1 hour saving tens of millions annually.”
Read how Memcyco was recognized by Datos Insights for real-time ATO protection.
Real-time ATO protection: the path forward for banks
Banks that fail to adapt will face growing fraud losses, reputational damage, and regulatory penalties. Legacy tools, MFA and takedown monitoring are reactive, not protective.
Banks that fail to adapt will face growing fraud losses, reputational damage, and regulatory penalties. MFA provides an important layer of defense, but it can be bypassed, while takedown monitoring is reactive rather than truly protective.
In contrast, real-time account takeover protection empowers banks to:
- Intercept attacks before customers are exposed.
- Safeguard trust while minimizing friction.
- Reduce fraud handling costs and operational strain.
- Stay ahead of compliance requirements.
Next step: Is your bank prepared for the ATO arms race?
Book a demo with Memcyco to see how proactive ATO prevention reduces fraud and restores customer trust.
If you prefer to explore strategies first, get our Industry Brief: Account Takeover Protection for Banks in 2025 for actionable guidance on building real-time defenses, staying compliant, and protecting customer trust.
FAQs
How does account takeover protection work?
It prevents attackers from using stolen credentials by intercepting sessions, deploying decoys, and analyzing devices in real time.
Why isn’t MFA enough for banks in 2025?
Attackers bypass MFA with adversary-in-the-middle kits. Customers also resist friction-heavy login flows.
What role does generative AI play in ATO fraud?
Generative AI automates phishing site creation, voice scams, and customer deception, making fraud faster and more scalable.
How can banks measure ROI on ATO protection?
By tracking reduced fraud losses, incident response time, and customer retention rates.
Will regulators force banks to reimburse ATO fraud losses?
Yes. The UK already mandates reimbursement, and similar measures are under review in the US.
Learn more in Memcyco’s Account Takeover Protection library.